I’ve been tacking in the direction of cybersecurity in recent years and specifically within the Microsoft 365 suite. I took the Security Administrator track on my Enterprise Admin certification and didn’t find that too difficult as it was grounded in my day-to-day. This one was pushing the boat out as it’s more Azure-based and honestly I wasn’t expecting to pass first time, but it fairly soaked up these dull days between Christmas and New Year!
I planned my preparation around Mark O’Shea’s intunedin.net blog post which is a great reference (I also used his reference for my MS-500 exam previously).
I won’t share specifics about the exam for obvious reasons but I’ll relate some stories of my experience that were helpful to me.
I’m relatively new to Sentinel but much of its functionality rests on KQL and I’ve spent enough time on advanced hunting in M365 Defender to have gained a grasp of the basics. My go-to is the cheat sheet on the now-archived MDATP Github and my favourite example is still the three-line detection which I was able to quickly get into action to counter the Follina vulnerability last year:
DeviceProcessEvents
| where ProcessCommandLine contains "msdt.exe"
| where InitiatingProcessFileName has_any (@"WINWORD.EXE", @"EXCEL.EXE", @"OUTLOOK.EXE")
Also, shout out to Must Learn KQL which has some great material and KQL Search which has a query for every imaginable circumstance.
Due to education licensing restrictions (don’t get me started on that) we have a small number of staff who are using devices without Intune licenses so they don’t get the policies for ASR (attack surface reduction) applied automatically. To ensure their devices are secured, I had to enable the policies via Powershell on these machines. There are two commands, Set-MpPreference and Add-MpPreference; whatever is set will be the only setting and whatever is added is added to it. The documentation does point that out, but it’s rather unhelpfully buried at the bottom of the article while at the top it simply says “type one of the following cmdlets” as though they both do the same thing.
We have Defender for Office365 and use the Safe Attachments feature for all staff and students. Our accounts team receives a lot of invoices through the day and they sometimes query these over the phone. I thought it would be helpful to enable Dynamic Delivery for them, since that way they would immediately see when messages arrive even if the attachments hadn’t been scanned yet. However, we kept receiving complaints from them that emails took a long time to open. I turned off Dynamic Delivery and they thanked us for fixing the problem. Sometimes a feature that helps some is a hindrance to others 🤷🏽♂️
Defender for Endpoint is a huge system and it can be daunting to make configuration changes after widespread deployment, but there are some critical features that should be examined; tamper protection, EDR in block mode, XDR connections and automated investigations. These are covered in detail in this blog post. One that has tripped me up in the past is MDE switching to passive mode by default when another AV is detected. An attacker could work around protections by installing an AV engine they control, creating exclusions in it and leveraging those to gain unauthorised access. Even when deploying in active mode, enabling EDR in block mode will prevent this.
Managing alerts for Defender for Endpoint can be tricky too. I want to be notified when malware is detected on a device in my organisation and I thought I had configured the rules appropriately. However, where MDE automatically remediates an alert, such as by removing malware, it is assigned a severity of informational as in this recent example:
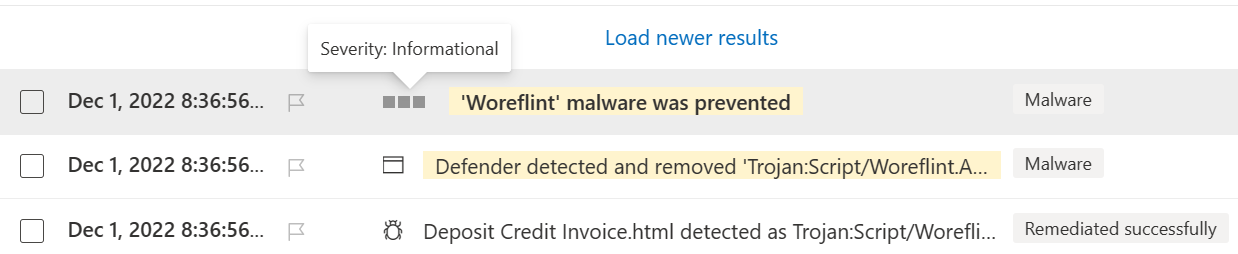 Since I hadn’t tagged informational-level alerts for my notifications, I wasn’t seeing these and missed the opportunity for a closer follow-up at the time. It’s a pity that notifications can’t be filtered by any attributes of an alert, so as to have one that always triggers on malware - without requiring the expensive Power Automate integrations at least.
Since I hadn’t tagged informational-level alerts for my notifications, I wasn’t seeing these and missed the opportunity for a closer follow-up at the time. It’s a pity that notifications can’t be filtered by any attributes of an alert, so as to have one that always triggers on malware - without requiring the expensive Power Automate integrations at least.
All the best to anyone attempting this tough exam!